Why We Need Cybersecurity Compliance
Cybersecurity compliance for defense manufacturers is a hot topic. With digital transformation reaching every corner of the manufacturing world, keeping systems secure isn’t just a technology issue—it’s a business imperative.
Over the past decade, several defense contractors—including Lockheed Martin, Boeing, and BAE Systems—have experienced significant cyber breaches , leading to the unauthorized acquisition of sensitive data by foreign adversaries.
These incidents highlight the ongoing challenges defense contractors face in protecting sensitive information from sophisticated cyber threats posed by foreign adversaries.
Manufacturers are now a prime target for cyberattacks. For those involved in defense work, compliance with cybersecurity regulations isn’t optional—it’s a necessity.
What We’ll Cover
This article discusses the cybersecurity regulations required for manufacturers working with the Department of Defense (DoD).
Specifically, we’ll look at NIST SP 800-171 and its role in the Cybersecurity Maturity Model Certification (CMMC), and Defense Federal Acquisition Regulation Supplement (DFARS) requirements, including how these relate to each other.
We’ll also discuss building a roadmap to compliance, common pitfalls, and provide resources for taking next steps.
We want to help manufacturers understand what it takes to meet these standards. Many of these requirements are achieved through good, old-fashioned cyber hygiene.
Overview of NIST SP 800-171, CMMC, and DFARS
When working on defense contracts or with Controlled Unclassified Information, manufacturers must comply with certain cybersecurity standards to safeguard sensitive information.
NIST SP 800-171 (and 800-172), CMMC, and DFARS are separate—yet related—sets of regulations that must be followed in order to ensure cybersecurity compliance when working with the DoD. While each set is managed by different organizations or programs, there is a great deal of overlap when it comes to the regulations themselves.
In general, NIST SP 800-171 provides the framework for cybersecurity controls for both CMMC and DFARS, with the main differences arising through assessment and certification.
What is NIST SP 800-171?
NIST: National Institute of Standards and Technology
NIST SP 800-171 is a set of cybersecurity guidelines created by the National Institute of Standards and Technology (NIST), with the SP standing for Special Publication (here on out we’ll just refer to it without the SP). It’s designed to protect Controlled Unclassified Information in non-federal systems and organizations. These standards are commonly required for contractors working with the U.S. federal government, particularly defense and other sensitive sectors.
The requirements cover a range of security practices across 14 categories, including access control, incident response, and encryption, with the aim of safeguarding sensitive data from unauthorized access and cyber threats.
NIST 800-171 relies on self-assessment to determine compliance.
NIST 800-172 builds upon these requirements, adding enhanced measures to defend against sophisticated threats. Compliance is also generally self-assessed, but third-party auditors or assessors may be required.
What is CMMC?
CMMC: Cybersecurity Maturity Model Certification
The CMMC program is managed by the Cyber Accreditation Body under the guidance of the DoD and is designed to enhance cybersecurity standards among its contractors.
It’s divided into different levels, each representing a tier of cybersecurity maturity and adopts the same 110 security controls as NIST SP 800-171, but it can differ in how compliance is assessed and enforced.
The NIST and CMMC frameworks are conceptually similar, but CMMC enforces stricter oversight. CMMC also introduces a formal certification process, which ensures compliance with NIST SP 800-171 and any contract-specific requirements.
CMMC Levels
Note: For aerospace and defense industries, higher levels are typically necessary due to the sensitivity of the information involved.
CMMC Level 1: Basic
- Includes 17 practices based on FAR 52.204-21.
- Protects Federal Contract Information.
- Requires annual self-assessment.
CMMC Level 2: Advanced
- Aligns with NIST SP 800-171.
- Includes 110 practices to protect Controlled Unclassified Information.
- Requires either self-assessment or third-party certification, depending on the contract.
CMMC Level 3: Expert
- Protects Controlled Unclassified Information from Advanced Persistent Threats.
- Based on a subset of NIST SP 800-172.
- Requires government-led audits.
What is DFARS?
DFARS: Defense Federal Acquisition Regulation Supplement.
DFARS is a set of regulations used by the DoD to supplement the Federal Acquisition Regulation and governs DoD-specific procurement and acquisition processes, including cybersecurity requirements within clause 252.204-7012.
NIST SP 800-171 provides the control framework for DFARS 252.204-7012, but DFARS enforces compliance through contracts and reporting requirements.
For contracts requiring enhanced protections, the DoD could instead specify NIST SP 800-172 in the contract’s terms or security requirements.
Why Compliance Matters for Defense Contracts
Cybersecurity compliance for defense manufacturers isn’t just a matter of paperwork—it’s about building trust and securing critical information that’s vital to national defense.
For customers in aerospace and energy sectors, compliance also serves as a signal of reliability and risk mitigation.
Federal procurement teams are especially concerned with reducing risk, and working with a manufacturer that meets these stringent requirements ensures that sensitive data and operations are safeguarded, ultimately reducing supply chain vulnerabilities.
Non-compliance can result in losing existing contracts or being disqualified from future work. The stakes are high, but with the right steps, compliance is achievable.

A U.S. Navy aircraft carrier seen from above. If you want a contract with the U.S. Department of Defense, you’ll need to be meet compliance regulations. Kalyakan / Adobe.
Overview of the NIST 800-171 Requirements
NIST 800-171 may sound daunting with its 110 requirements, but they can be broken down into smaller, more manageable categories.
Requirements are organized into 14 families, each addressing different aspects of cybersecurity, including:
- Access Control: Managing who has access to your systems.
- Awareness and Training: Ensuring employees know how to keep information secure.
- Audit and Accountability: Monitoring systems to ensure appropriate use.
- Configuration Management: Maintaining secure configurations for hardware and software.
- Identification and Authentication: Making sure only authorized individuals access the system.
- Other key areas include Incident Response, Risk Assessment, and Security Assessment.
Basic Cyber Hygiene Practices
One of the good things about NIST 800-171 is that a lot of the requirements can be met through basic cyber hygiene. In other words, if your company is already following common-sense security practices, you’re off to a good start.
Let’s look at some of the requirements that manufacturers can meet without too much difficulty:
Access Control
Implementing user management practices, such as role-based access control and enforcing strong password policies, are relatively straightforward. By ensuring that employees only have access to the information they need, you minimize the risk of unauthorized data exposure.
Awareness and Training
Conducting regular training sessions for employees about phishing, password hygiene, and safe online practices can tick off several requirements. Specialized training for engineering teams might also be needed, particularly for those working on sensitive aerospace or energy projects, to ensure they understand the unique cybersecurity challenges in these sectors. This training can be done internally or through simple online modules that emphasize the role each individual plays in maintaining security.
Physical Protection
Often overlooked, physical security measures are part of the requirements. Making sure that only authorized personnel have access to servers and network equipment is an easy win. It might be as simple as locking a server room or having sign-in procedures for visitors.
For circumstances where a locked server room isn’t available, a reasonable precaution is to disable any unused ports on your networking gear and tie all used ports to the MAC address of specific connected devices. This will go a long way to prevent unwanted devices from connecting via physical ethernet.
Tackling the More Challenging NIST 800-171 Requirements
Of course, not all NIST 800-171 requirements are easy to implement. Some are more challenging, especially for smaller manufacturers with limited IT resources. Let’s talk about a few of the harder ones and some strategies to tackle them.
Note: For organizations needing to comply with NIST 800-172, additional requirements such as advanced threat monitoring and enhanced data protection protocols will also need to be addressed.
Encryption
Encrypting data, at rest and in transit, can be technically complex and requires specific tools. To comply, manufacturers must ensure that sensitive data is always encrypted—whether it’s being stored on a server or sent via email.
Implementing encryption can mean upgrading systems and working with IT professionals who have expertise in cybersecurity. Procurement and engineering teams may be concerned about the costs and logistics involved in encryption upgrades, but there are potential cost-effective solutions, such as open-source encryption tools or grants and funding options available to assist with this transition.
Incident Response
One of the key challenges to compliance is having a documented incident response plan. This isn’t something you can just install; it requires thought and preparation. To simplify, start by defining what constitutes an “incident” and outline a basic step-by-step response process. Assign clear roles and responsibilities—who needs to do what when something goes wrong.
Risk Assessment
Conducting a risk assessment means evaluating vulnerabilities and documenting them. This task can be overwhelming, but the key is to start small. Identify your most critical assets—like servers or key databases—and evaluate potential risks. You can also hire external experts to conduct a thorough assessment and provide you with insights into areas of concern.
Roadmap to Cybersecurity Compliance for Defense Manufacturers
For defense manufacturers trying to navigate compliance, a roadmap can make a huge difference.
Timelines for achieving compliance can vary significantly depending on the size and complexity of the manufacturer.
Including a clear NIST 800-171 compliance timeline for manufacturers can help federal procurement teams understand realistic expectations for becoming compliant.
Smaller manufacturers may be able to implement the steps more quickly, while larger organizations might require more time to align their various departments.
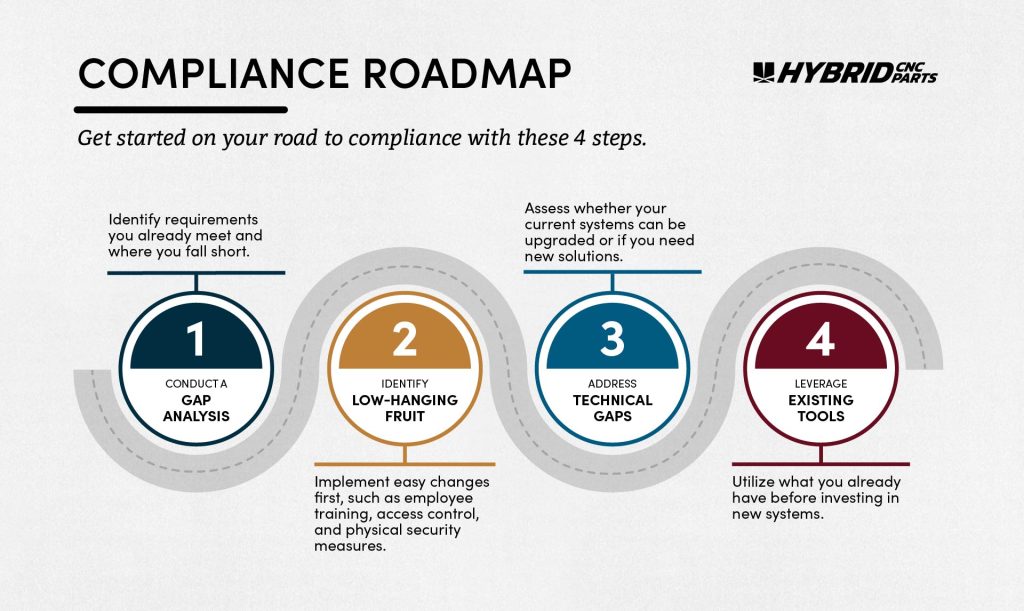
Here’s a suggested step-by-step approach to achieving compliance:
- Conduct a Gap Analysis: Identify what requirements you already meet and where you fall short.
- Identify Low-Hanging Fruit: Implement the easy changes first, such as employee training, access control, and physical security measures.
- Address Technical Gaps: For more technical requirements, like encryption and incident response, assess whether your current systems can be upgraded or if you need new solutions.
- Leverage Existing Tools: Chances are, some of your existing IT infrastructure can be used to meet the requirements. Make sure you’re utilizing what you already have before investing in new systems.
Common Cybersecurity Pitfalls and How to Avoid Them
Achieving compliance comes with its challenges, and there are common pitfalls manufacturers should be aware of:
- Underestimating the Importance of Documentation: Compliance is as much about demonstrating your practices as it is about the practices themselves. Ensure that everything—from policies to incident responses—is well-documented.
- Ignoring Employee Training: Human error is one of the most significant causes of security incidents. Make training a recurring part of your process, not a one-off event.
- Neglecting Continuous Monitoring: Compliance isn’t a “set it and forget it” exercise. Continuous monitoring and regular assessments are necessary to ensure that your cybersecurity practices evolve with emerging threats.
Quick Cyber Hygiene Wins
We’ve mentioned basic cyber hygiene, but what does that mean?
Basic cyber hygiene forms the foundation of compliance. Regular software updates, strong passwords, access control—these are all low-cost, high-impact practices that go a long way toward satisfying NIST 800-171 requirements.
For manufacturers in the aerospace and energy sectors, these basic practices are often a prerequisite for more advanced compliance, reassuring potential customers that they can build upon a solid foundation incrementally.
Many manufacturers underestimate the power of these simple steps, but they form the bedrock of a strong cybersecurity posture.
Consider the example of an aerospace CNC manufacturer that regularly updates software and ensures employees changed their passwords every few months.
When a phishing attack targets this manufacturer, the quick response and effective password management should limit the impact, demonstrating the power of strong cyber hygiene practices and defense contractor compliance.
Beyond Compliance: The Broader Benefits of Cybersecurity Compliance for Defense Manufacturers
Complying with NIST 800-171 or NIST 800-172 isn’t just about meeting contractual obligations.
It also has broader benefits, such as building trust with customers and partners, and protecting your business’s intellectual property.
Additional Resources and Next Steps
If you’re ready to start your compliance journey, there are a wealth of resources available to guide you.
Useful Links and Guides
The official publication of NIST 800-171 provides in-depth explanations and guidelines for each requirement.
Information about CMMC from the U.S. Department of Defense.
DFARS 252.204-7012 : Safeguarding Covered Defense Information and Cyber Incident Reporting.
Templates and Tools
Look for cybersecurity templates and tools that can help you create policies and conduct assessments, like the DOE SBIR/STTR Cybersecurity Self-Assessment (PDF) .
Staying Up to Date
The Cybersecurity and Infrastructure Security Agency (CISA) provides national coordination for critical infrastructure security and resilience. The CISA website lists cybersecurity alerts and advisories , and its mailing list is a great resource for regular updates on recently discovered exploits and problems.
When to Seek Professional Help
If you find some of these requirements beyond your capability, consider hiring an Managed Security Service Provider to help fill in the gaps. Triton Technologies is one option that has experience in cybersecurity compliance for defense manufacturers.
Conclusion
To recap, cybersecurity compliance for defense manufacturers is crucial for working with the DoD. It helps protect sensitive information, builds trust, and secures contracts.
Many of the requirements are simply about implementing good cybersecurity practices—like access control, training, and monitoring—while others may require a bit more expertise and planning.
The key is to break it down, start small, and keep moving forward. Compliance may seem overwhelming, but with a systematic approach, it becomes manageable. Start by assessing where you stand, make improvements, and don’t hesitate to seek external support if needed.
Your cybersecurity posture is not only vital for compliance—it’s an asset for your business.
We believe strongly in supporting a secure future for domestic manufacturing—feel free to reach out if you have questions or need a supplier that takes cybersecurity seriously.
We Are Compliant
Hybrid CNC Parts takes compliance and risk mitigation seriously.
Contents
Contents